Who We Are
Our team is composed of seasoned professionals with extensive experience in security and risk management. They bring with them a solid background in safeguarding corporate assets across complex environments.
We complement this core team with top specialists in physical, electronic, and IT security to provide comprehensive protection solutions tailored to your needs.


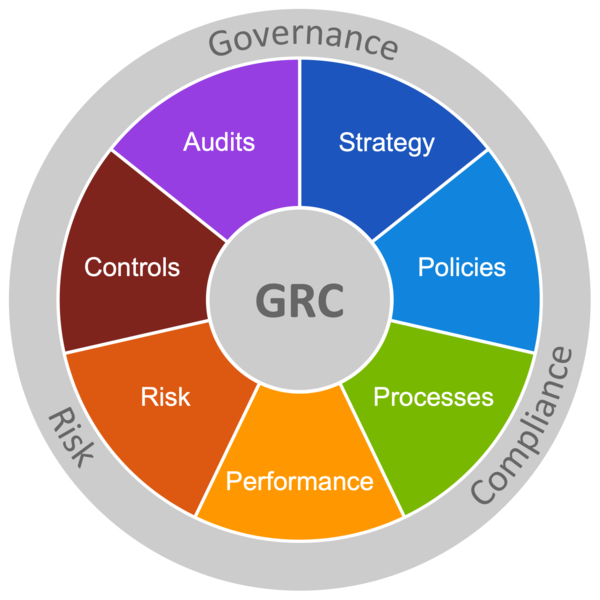
Audit
- Risk management policy
- IT / Communication / data processing systems
3 steps:
-
- Strategic evaluation
- Identification of key elements that need to be secured
- Governance control and management
- Risk management Strategy
- Security controls
- Operational phase procedures
- Communication related to the security strategy
- Incident and crisis management
- Elementary evaluation
- Regulatory compliance
- Information and training
- Access control and identity management
- Detection & Response
- Information management and data confidentiality
- System protection
- Infrastructure security
- Organizational resilience
- Advanced evaluation
- Organization & Governance
- Risk Management
- Identity and Access Management IAM
- Cloud Management and Security
- Application Security
- Supply Chain
- Connected Industrial Tools
- Internet of Things IoT

We provide discreet and effective protective measures and source the right team for all types of activities, business or personal travel, and for your loved ones.
We also offer country-specific risk analysis and can train your teams or family members on the social and cultural aspects of the destination country.

- Developing and achieving complex technical projects
- Recommending technical solutions tailored to client needs and orientations
- Managing the entire work chain: from supplier sourcing to project delivery.
This includes site visits and project acceptance processes.


Business Support Approach

Business Development

Business Support
Protecting a company’s assets requires a global, long-term vision.
We are also focused on protecting your data and IT/OT environment.
We work with experts in cyber security and IT Security to deliver the best evaluation and mitigation prescription.
We can provide a wide range of services from SOC, pentesters, consultants.

- Technical solutions for improving safety and security
- Drone detection
- Autonomous drone detection solution (drone in a box)
- Tethered drone detection solution
- Other solutions recommended following site audits
- Security study: access control, intrusion, video surveillance
- Security and safety equipment
- Safety/security process improvement: audit and review of existing procedures
.jpg)
Drone Detection
- Technology based on passive radio frequency detection of drones and their remote controls.
- Completely passive, no interference with existing equipment.
- Based on a proven solutions (various types of sites equipped).
- Range depending on solution chosen and sensor installation.
- Local and remote operation possible (internet connection required).
- Easy installation: on a high point within sight of the horizon, 220V power supply, internet connection for remote operation.
- Mitigation from a fixed position, integrated to the solution or hand-portable.

- Technology based on a drone operated from a lightweight docking station
- Top of the on-the-shelf line
- Unique patent for battery replacement technology for extended operating time
- Using high-end drones from French manufacturers or other brands
- Get a tailored drone and payload to your needs
- 100% WEB-based management software
- Heavy-duty solution available upon request
- Multiple-sites management platform of boxes
- Integration into VMs, PSIMs, Hypervisors.